

 |

|

The average rating for Cyberthreats: The Emerging Fault Lines of the Nation State based on 2 reviews is 2 stars.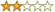
Review # 1 was written on 2013-02-11 00:00:00 James Dunevent James DuneventThis book would have rated more stars from me if not for the final chapter, "Where Do We Go From Here?" The first 200 pages are an in-depth examination of the dichotomy between how states handle internal and external threats, with particular attention paid to the US method of handling each separately, the internal (crime and terrorism) responded to by law enforcement officials and external (war) responded to by the military. Brenner makes a compelling case that the line between the two, internal and external is becoming blurred due to the introduction of cyberspace, cyber operations, and cyber threats. She points to the challenge of attribution of attack (what "kind" of attack is taking down a banking system? Is it a crime or does it tend toward an act of war? What about a power grid? If it's an act of war, what do we do if the perpetrator is not a nation-state, but an individual or group? What if they are sponsored by a nation-state)? All of these questions lead into the second major attribution problem, which is actor attribution. Even if we can pinpoint an IP address, can we be certain where it sits geographically? If we can, can we be certain who was sitting in front of the terminal at the time? Were they acting in a "state" capacity, or privately? All of these issues create complexity and fog regarding how we respond to threats. Where Brenner loses me is in her recommendation for how to address the challenges. They boil down to creating a civilian volunteer cyberforce that would police the internet, reporting suspicious activities and suspected threats. The whole thing smacks of the Stasi to me. I can see my neighbor reporting my suspicious activity to the government. She also believes that it would be a pretty easy thing to a) allow law enforcement officials share intelligence with the military regarding threats so that they can determine "if they constitute war," which doesn't sound like something the American people would be to fond of, even if significant controls were put in place. Either way, it's much tougher than the picture painted in the book. Finally, Brenner seems to advocate some relaxation of Posse Comitatus in order to create an agency a fused "internal-external" threat institution (read: powers of both law enforcement and the military) to exist in cyberspace. (p. 294). "I, for one, do not find the prospect of an internal-external response institution operating in cyberpace particularly discomfiting" going on to point out that because she couldn't "see" them and it would not "literally involve sending military personnel into cyberspace to act as law enforcement officers," it wouldn't be a huge deal. I have to beg to differ on the entire tone of the argument. I'm not sure how many folks would be on her side with this prospect. The amount of uproar from rumors about the NSA's involvement NOW leads me to believe an agency with such power would be anything but easy to stand up, at least given American sentiment today. Perhaps a cyber event will inspire more folks to ease up on their concern, but I don't see it happening. |
Review # 2 was written on 2013-04-22 00:00:00 Luke Clare Luke ClareGood coverage of the laws relating to the use of force / armed attack. Would be helpful to any attorney/officer who deals with when the use of force is appropriate. |
CAN'T FIND WHAT YOU'RE LOOKING FOR? CLICK HERE!!!